This Is A Vulnerable Time
There are a lot of unscrupulous people out there, and they want your company’s money, data, and resources. These bad actors are taking advantage of the upheaval and confusion of quarantine, because they know that our defenses are down.
We are concerning ourselves here with phishing — the use of communication systems (like email) to attempt to lure people into traps. Phishing is like dipping a baited hook into the water (hence the name) with the hope that a random fish will bite. But the phishers are often sophisticated enough to make their bait look legitimate.
How Bad People Try To Trick Us
We are all used to receiving spam email from random people, and that is easy to ignore. But when we get an email from a colleague, or from a known company, our defenses can be lowered. Here are some examples, purporting to be from our friend Damien Clark:
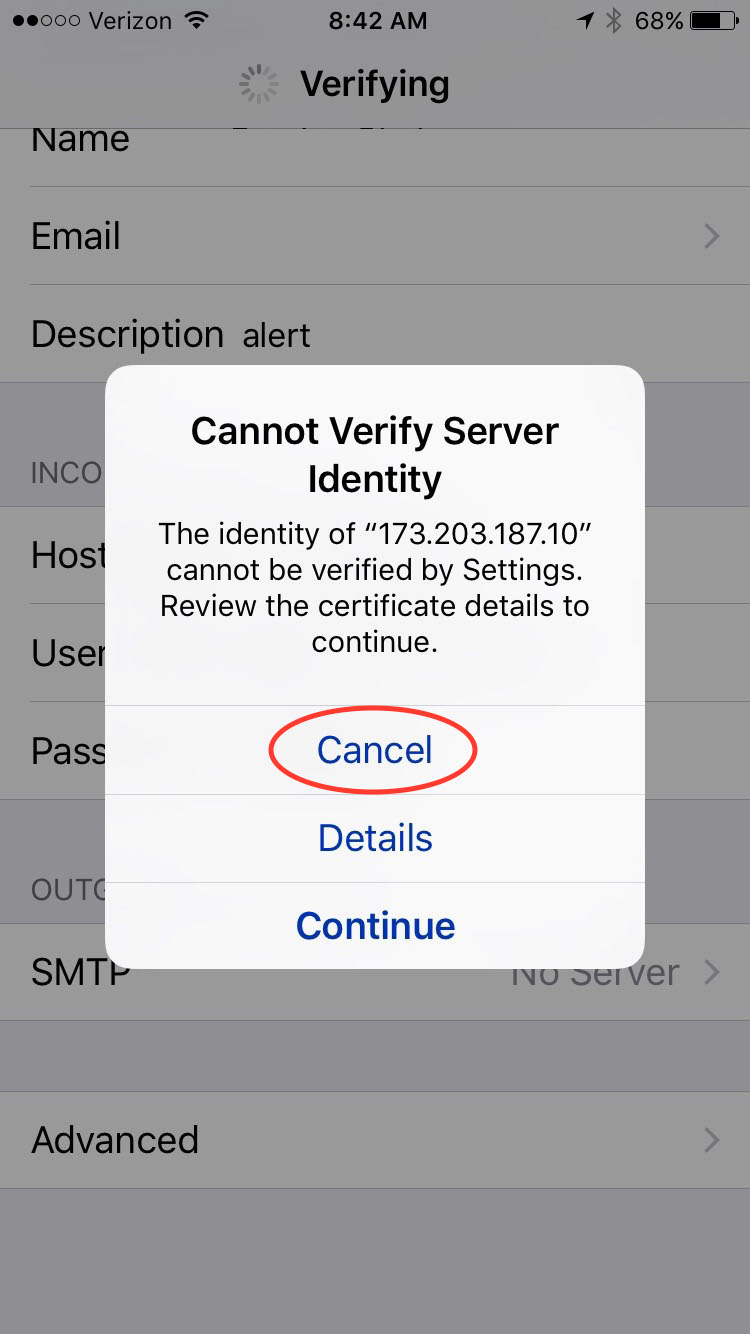
The from name can be a lie
From: Damien Clark <[email protected]>
Subject: I have an urgent request
I am in a meeting but I need your help. Send me your cell phone number so we can text.The sender’s name on an email is like the return address on an envelope. Senders can put whatever they want there. Notice that the email address does not match up with the name.
The from address can be a lie
From: Damien Clark <[email protected]>
Subject: I have an urgent request
I am in a meeting but I need your help. Send me your cell phone number so we can text.This one is tougher to spot. The email address looks correct, but on closer inspection we can see that one letter is off. Scammers have even been able to use non-English characters which look exactly the same as their English counterparts, rendering visual confirmation impossible.
A mailbox could be compromised
From: Damien Clark <[email protected]>
Subject: I have an urgent request
I am in a meeting but I need your help. Send me your cell phone number so we can text.This example was actually sent from Damien’s mailbox. But Damien did not send it. Somebody has his password!
Emotional plea
From: COVID-19 Task Force <[email protected]>
Subject: Employer work space COVID-19 respiratory system virus spread reduction guidance
Kindly discover attached!
Attachment: covidinfo.lnkHere we have an email with what seems like an important attachment. But click it, and you will be redirected to what looks like a password entry page for your email account. Once you enter your password, the scammers have it.
Technical plea
From: Feedwire Technical Support <[email protected]>
Subject: Email_Disconnection
Your account [email protected] will be disconnected from feedwire.com. if you failed to resolve the errors on your mail. Click here to resolve now.This seems important! But any email with a link that asks for your password should be viewed with the highest degree of suspicion.
Why Scammers Are Doing This
It is easy to think that you will not be a target for these types of behavior, or that there is not anything to be gained from compromising your email account. But everybody is a target. Once a scammer has a successful phishing expedition, there are several common things that come next.
Accessing your email account
When somebody has access to your email account, they can immediately attempt the same scheme on everybody in your address book. These attacks can spread through the company quickly. And each compromised account may be full of valuable information.
Accessing your other accounts
If you have used the same password somewhere else, then they have access to that as well. They can also reset passwords to any accounts that are secured by your email address.
Directing your conversation from email to text
There are plenty of systems in place to audit and control access to email accounts and the information therein. But if a scammer can move the conversation to text, those systems are bypassed.
Convincing you or your colleagues to send them money
Once your trust has been gained, the scammers frequently try to get money. This may be anything from advanced wire fraud to simply asking you to pick up some gift cards for them. They may target you or they may target your colleagues using your own compromised mailbox.
What we all need to do about it
Phishing is a type of social engineering — psychological manipulation of people into performing actions or divulging confidential information. The best way to defend yourself against social engineering is through educating yourself and taking ownership over your own security.
Vigilance
There are technical measures in place to prevent scams, but none of them are perfect. Human beings are still much better at noticing ill intent than computers are. Approach every communication with a healthy level of distrust.
Scrutiny
Examine emails closely. If you are asked for any information, or to do anything for somebody, make certain that it is a legitimate request. If you are not sure, ask IT!
Remember: Any email with a link that asks for your password should be viewed with the highest degree of suspicion.
Verification
If you are unsure of the legitimacy of an email, call the sender. Scammers may be rudely aggressive about being too busy for a phone call — do not be taken in by that.
Technical Measures
The human being receiving an email is the last line of defense. But there are plenty of technological roadblocks that reduce the risk significantly.
Two Factor Authentication
Your ATM PIN is useless without your ATM card. So too your password is useless if you also need to have your smartphone to log into a computer. Two factor authentication makes sure you have an app on your smartphone before you can connect. Even if your password is compromised, your account is safe. (When scammers do get a password, they may try to trick you into providing the code from your phone. Be vigilant!)
Name Impersonation Settings
Email servers can watch for email that uses the name of a company employee but comes from an email address outside of the company. Sometimes these are legitimate, but often they are not. A warning banner at the top of an email reminds recipients to exercise extra caution.
Email Security
Technologies such as DKIM, DMARC and SPF help to stop spammers from impersonating people, and provide data about who is trying. This is something we can do on the back end to cut down the flow of illegitimate emails.
Don’t Panic
Feedwire can help with training and simulations to improve your scrutiny chops, and with technical measures to reduce the frequency of scams that reach you as well as the likelihood that a scam will result in a successful compromise of your mailbox.